
Hey everyone! Welcome to our web safety blog. Today, our Senior Consultant Ravi is here to talk about the XML Signature Wrapping (XSW) attack. Now, don’t worry if that sounds a bit fancy – we’re going to break it down into simple bits.
So, you know when you get a message on the internet, and there’s a digital stamp saying “Signature Valid” or “Digitally Signed”? That’s an XML signature. Imagine a notorious person messing with that stamp, making it look like everything is cool when it’s not. That’s what the XML Signature Wrapping attack does – it tricks the system into accepting sneaky changes to the message.
Through this blog, you will understand the workings of this sneaky attack, and explore strategies to safeguard our online stuff. By the end, you will be equipped to protect your digital world like a superhero. Ready to dive in and become a web safety expert? Let’s go!
An XML Signature is a cryptographic method used to ensure the integrity, authenticity, and origin of an XML document. It involves creating a digital signature that is attached to the XML document. This signature is generated using a private key and can be verified using the corresponding public key. If the signature is valid, it indicates that the document has not been tampered with and comes from a trusted source.
Consider the following XML document:
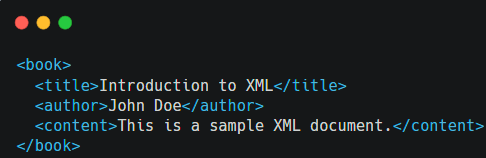
Now, let’s create an XML Signature for this document. The process involves:
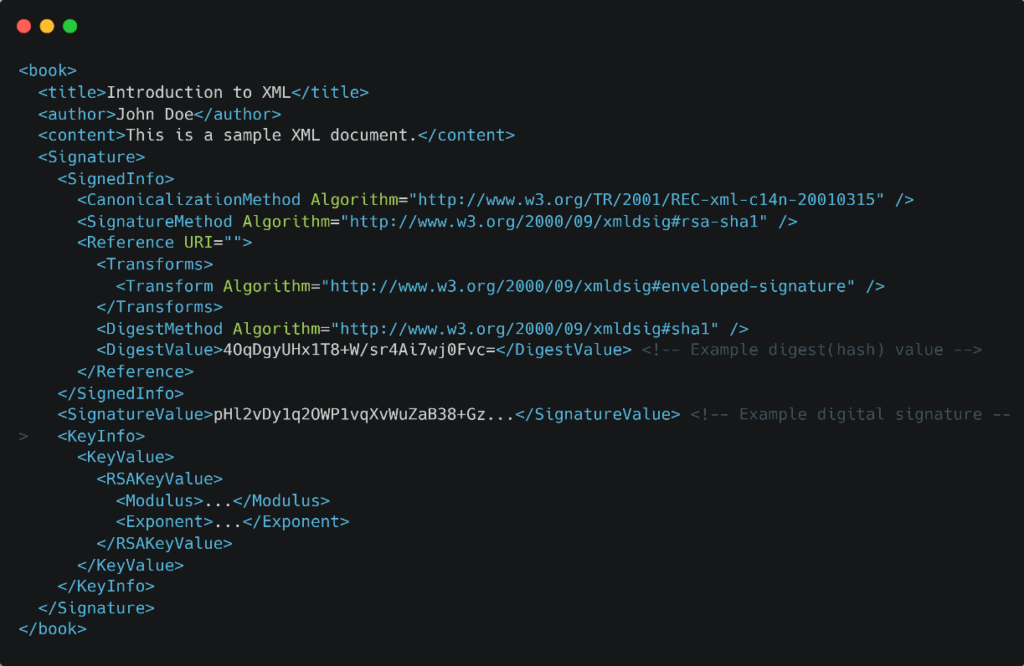
In this above example:
These details collectively make up the XML Signature, ensuring the secure and verifiable signing of the XML document.
In real-world scenarios, XML Signatures are commonly used in web services, electronic transactions, and various other applications where data integrity and authenticity are crucial. They provide a secure way to ensure that the XML content has not been tampered with during transmission or storage.
An XML Signature Wrapping (XSW) attack is a security vulnerability where an attacker manipulates the XML signature of a document to deceive a system into accepting unauthorized changes. This attack exploits weaknesses in the validation process of XML signatures, allowing the malicious insertion of additional elements or modifications to the XML content while preserving the integrity of the original signature.
Consider a scenario where a financial application processes XML requests for fund transfers. The typical XML structure includes the transaction details and a digital signature:
Now, an attacker attempts an XSW attack by duplicating the “amount” element and its corresponding signature:
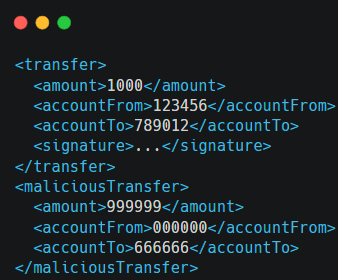
In this manipulated version, the attacker adds a new “maliciousTransfer” element with altered transaction details but retains the original signature. If the system fails to properly validate the entire XML structure or doesn’t detect the extraneous “maliciousTransfer” element, it might process the unauthorized transfer specified in the malicious data.
This can lead to potential financial losses or unauthorized access, highlighting the importance of robust XML signature validation to prevent such XML Signature Wrapping attacks.
In a simple signature-wrapping attack, the attacker appends or modifies elements within the XML document while maintaining the original signature. This manipulation aims to deceive the system into accepting unauthorized changes without altering the signature, potentially leading to unintended consequences.
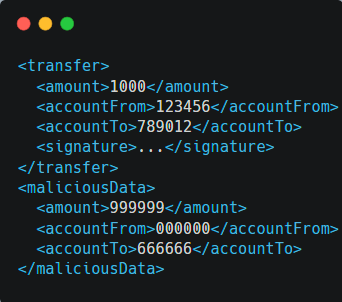
The original XML document includes a fund transfer with a valid signature.
The attacker introduces a new section, “maliciousData,” with altered transaction details but retains the original signature.
The system, if not validating the entire XML structure, might process the unauthorized transfer specified in the malicious data.
In this type, the attacker wraps the entire original XML signature along with a manipulated version. The objective is to trick the system into validating the wrapped signature, resulting in the acceptance of unauthorized changes.
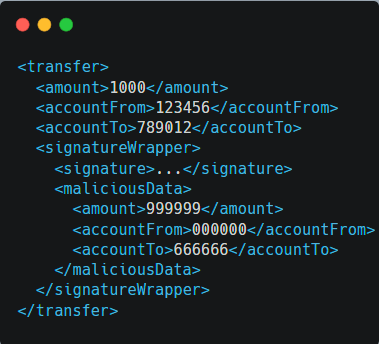
The attacker encapsulates the original XML signature along with a new section, “maliciousData,” within a “signatureWrapper” element.
The system, if not checking for the correct structure or validating the wrapped signature, may mistakenly process the unauthorized transfer specified in the malicious data.
In a multi-reference attack, the attacker includes multiple references in the XML signature, pointing to different parts of the document. This can confuse the validation process and potentially lead to the acceptance of unauthorized changes.
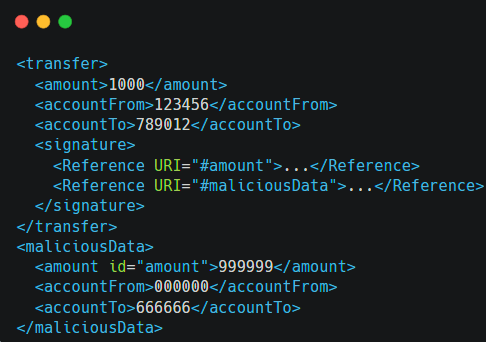
The attacker introduces multiple references within the XML signature, each pointing to different parts of the document, such as “amount” and “maliciousData.”
The system, if not handling multiple references properly, might validate only a part of the XML document, leading to the acceptance of unauthorized changes specified in the malicious data.
XML Signature Wrapping (XSW) attacks can have serious real-world implications, especially when sensitive data is involved. Here are some hypothetical scenarios to illustrate the potential impact of XSW attacks:
Scenario: A financial institution uses XML signatures to secure fund transfer requests. The XML document includes details like the amount, source, destination accounts, and a digital signature.
XSW Attack: An attacker intercepts a legitimate transfer request, and appends a new transaction with a higher amount and a different destination account while preserving the integrity of the original signature.
Impact: If the system doesn’t thoroughly validate the entire XML structure, it might process the unauthorized transfer specified in the malicious data, leading to financial losses.
Scenario: A healthcare system utilizes XML signatures to ensure the integrity of patient records. Each record contains details such as medical history, prescriptions, and treatment plans, along with a digital signature.
XSW Attack: An attacker modifies the medical history section of a patient’s record, introducing false information without invalidating the original signature.
Impact: If the system fails to detect the manipulated medical history during signature validation, healthcare professionals might rely on inaccurate information, potentially leading to incorrect diagnoses or treatments.
Scenario: An online service uses XML signatures to secure authentication tokens exchanged between clients and servers. The XML document includes user details, permissions, and a digital signature.
XSW Attack: An attacker intercepts a legitimate authentication token, and appends a new section granting additional unauthorized permissions while keeping the original signature intact.
Impact: If the system doesn’t validate the entire XML structure, the attacker gains elevated privileges, potentially leading to unauthorized access and actions on the service.
Scenario: A government agency uses XML signatures to secure official documents such as tax filings. Each document includes taxpayer information, financial details, and a digital signature.
XSW Attack: An attacker alters the financial information within a tax filing, introducing false data without invalidating the original signature.
Impact: If the system fails to detect the manipulated financial data during signature validation, it could lead to erroneous tax assessments and financial discrepancies.