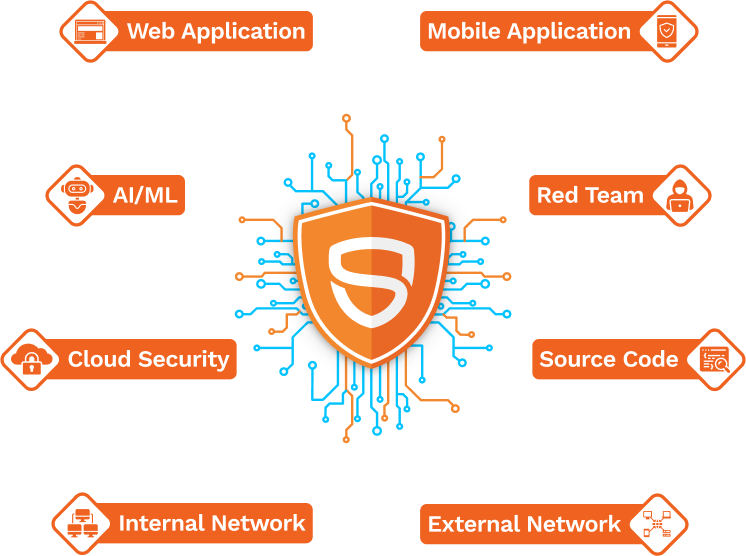
PROFESSIONAL PENTEST SERVICES
Human-led, AI-Augmented
-
Web Application Pentest
We take pride in going above and beyond the standards set by the industry, such as the OWASP
-
Internal Network Pentest
With the help of our internal network penetration testing service, you will discover exploitable vulnerabilities in your internal
-
External Network Pentest
The SecOps Group employs innovative technologies from RedHunt Labs to identify an organization’s publicly exposed digital assets and
-

Mobile Application Pentest
A deep-dive Mobile App Penetration Testing assessment is performed to identify weaknesses and ensure your mobile application security.
-

Source-Code Analysis
Finding and analysing the vulnerabilities at the source code level using the static code analysis. Our technical team
-

Cloud Security Assessment
Finding and analysing the vulnerabilities at the source code level using the static code analysis. Our technical team
-

Red Team Assessment
Our goal within a Red Team exercise is to conduct a full scope black-box test including, but not
-
AI/ML Pentest
Our AI/ML security experts specialize in pinpointing weaknesses in your AI/ML integrated applications. We safeguard them from attacks
Security Assessments
Client Satisfaction
Years of Experience
TRUSTED BY INDUSTRY LEADERS



















CLIENT SUCCESS STORIES
What security leaders say about working with us